Event Storming: A Collaborative Blueprint for Domain Modeling
Event Storming is a high-impact, collaborative workshop methodology designed to bridge the gap between domain experts and software practitioners. Developed by Alberto Brandolini, it provides a lightweight, visual framework for surfacing and understanding the dynamics of complex business domains before a single line of code is written.
At its core, Event Storming is about shared discovery. It brings together developers, architects, business analysts, product owners, and stakeholders into a facilitated, co-creative environment where ideas are surfaced in real-time, and insights emerge from dialogue—not documentation. Participants are encouraged to express their understanding of business workflows using sticky notes, color codes, and spatial relationships on a large canvas or digital board.
Unlike traditional modeling techniques such as UML or BPMN, which often require technical fluency and a formalized structure, Event Storming is intentionally informal and accessible. There’s no reliance on specialized tooling or standardized notation. Instead, it promotes raw exploration and open-ended collaboration using tools as simple as markers, sticky notes, and wall space. This lowers the barrier to entry for non-technical participants, ensuring everyone—regardless of role—can contribute meaningfully to the design conversation.
Event Storming is especially powerful in the context of Domain-Driven Design (DDD), where understanding and modeling the problem space is critical. It accelerates the discovery of domain events, aggregates, and bounded contexts by encouraging teams to think in terms of what happens in the business, not just how systems are built. It turns abstract concepts into tangible artifacts and provides the clarity needed to design modular, scalable, and business-aligned software systems.
In short, Event Storming isn’t just a workshop. It’s a strategic alignment exercise that unlocks tacit knowledge, exposes ambiguity, and lays the foundation for building the right system—with the right boundaries—for the right problem.
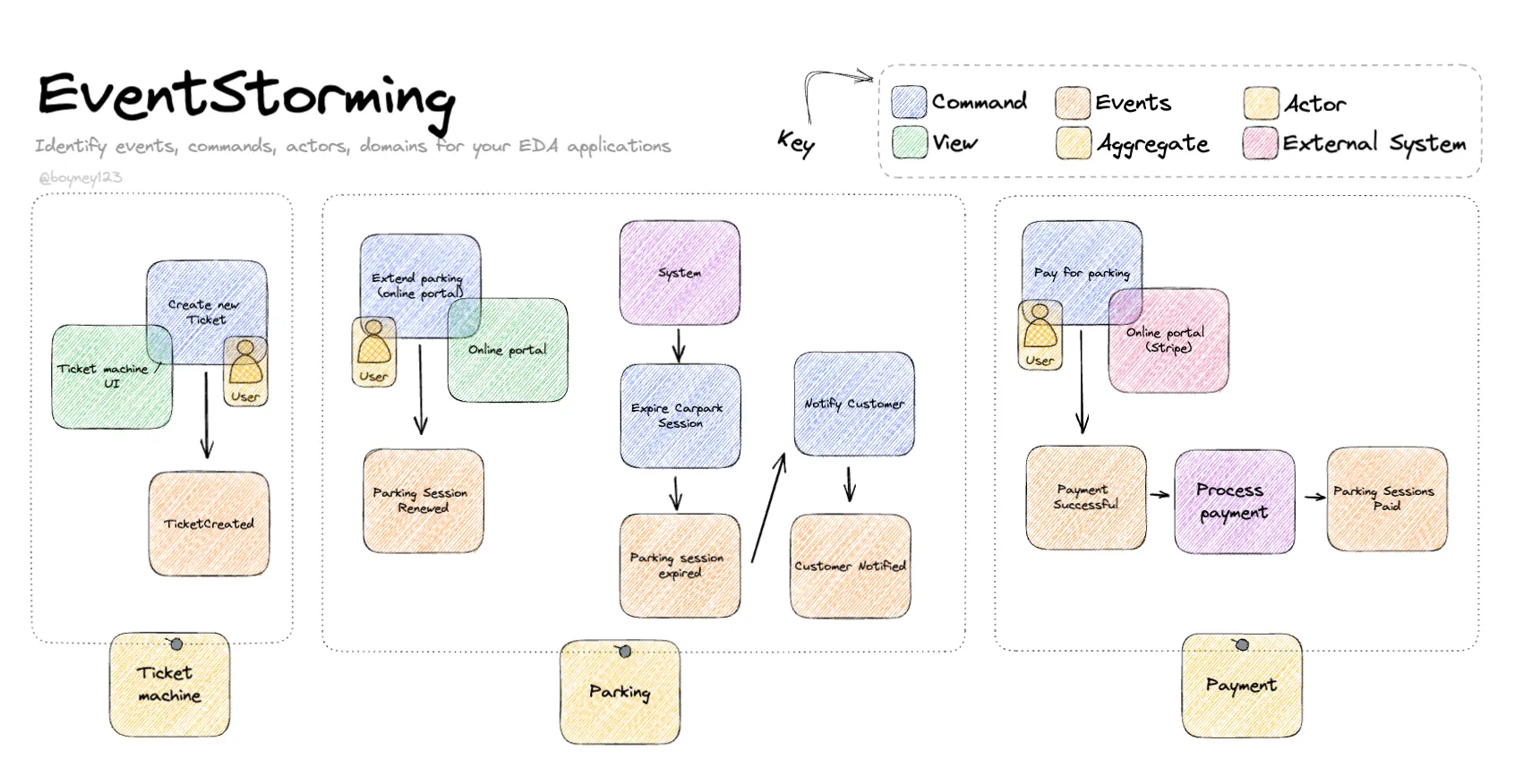
What is Event Storming?
Event Storming is a structured, hands-on workshop methodology aimed at visually modeling complex business domains through collective exploration and conversation. It focuses on identifying key domain constructs such as domain events, commands, aggregates, and bounded contexts, enabling teams to collaboratively unravel how a business truly operates—long before implementation begins.
At the heart of Event Storming is the idea that effective software starts with a deep understanding of the problem space. By bringing together developers, architects, product managers, business analysts, and domain experts in a single room (physical or virtual), the technique fosters a shared language and common understanding. Sticky notes become the medium, and the whiteboard becomes the canvas on which workflows, logic, and boundaries are made explicit.
Rather than diving straight into solutions, Event Storming deliberately emphasizes discovery over delivery. It provides the space to ask critical questions: What happens in the business? Why does it happen? How should systems respond? In doing so, it uncovers tacit knowledge, business rules, and edge cases that traditional specification documents often overlook.
This practice is especially favored in contexts such as:
- Domain-Driven Design (DDD): where domain complexity is high, and modeling must align tightly with business needs.
- Microservices architecture: where determining correct service boundaries is essential to maintain autonomy and cohesion.
- Event-driven systems: where understanding the flow of events and reactions is foundational to design.
By visualizing the domain from the perspective of business events, Event Storming enables cross-functional teams to identify what matters, eliminate ambiguity, and align on architecture and priorities. It’s not just a modeling tool—it’s a catalyst for creating better software through better communication.
Event Storming Step-by-Step
1. Extract Domain Events
Domain events are at the core of Event Storming—they represent facts that have occurred within the business domain. Unlike user actions or system intentions, domain events are immutable records of state transitions. They describe outcomes rather than intentions, and they are always expressed in the past tense.
Think of domain events as the business narrative: they are the observable milestones that describe what has happened, why it matters, and what should come next. These events capture essential behaviors and state changes that the business cares about.
In an e-commerce domain, for example, domain events might include:
Product added to cartShipping details confirmedPayment submittedOrder confirmedOrder shippedOrder delivered
Each of these events reflects a state change that has already occurred, and serves as a trigger point for subsequent processes, decisions, or reactions.
During an Event Storming session, these events are typically represented by orange sticky notes and are arranged left to right along a chronological timeline. This layout visualizes the flow of the business process over time—helping teams see not only what events occur, but in what sequence and under what conditions.
By focusing first on domain events, teams ground themselves in the reality of the business. It’s not about how the system should behave, but what must be true in the business domain. This prevents premature technical assumptions and creates a strong foundation for modeling logic and behavior later in the session.
Identifying domain events early also enables teams to:
- Clarify terminology across stakeholders (aligning language)
- Reveal hidden rules and edge cases
- Begin mapping bounded contexts based on event clusters
Ultimately, domain events serve as the backbone of the Event Storming model. They illuminate what really happens in the business—and why it matters.
2. Set Up Commands
In the Event Storming methodology, commands represent intentional actions—requests made by users or systems that are meant to initiate change within the domain. Unlike domain events, which describe what has already happened, commands focus on what should happen next. They are expressions of will, purpose, or desire to alter the state of the system.
Commands answer the question: “Why did this event occur?”
They are typically written in the imperative mood, signaling the action to be performed (e.g., Submit payment, Add product to cart). Importantly, a command does not guarantee that the resulting event will occur—only that an attempt to execute an operation has been made. The system may reject the command if validation fails or if certain business rules aren’t satisfied.
In an e-commerce domain, common commands might include:
Add product to cartConfirm shipping detailsSubmit payment methodPlace orderCancel order
These commands are visualized during Event Storming workshops using a distinct color (typically blue sticky notes) and are placed to the left of the event they are intended to trigger. This left-to-right positioning emphasizes the cause-and-effect flow: command → domain event.
Understanding commands is essential because:
- They initiate system behavior, tying user intent to business response.
- They help define service interfaces or API endpoints in implementation.
- They provide a natural foundation for command-handling logic in frameworks like CQRS (Command Query Responsibility Segregation).
- They clarify ownership of decisions—who or what initiated a change.
Moreover, mapping commands to events creates clarity around who acts, when, and why, which is instrumental in modeling aggregates, designing bounded contexts, and defining the responsibilities of microservices.
Ultimately, commands serve as the starting point for action within a system. Capturing them in the Event Storming process ensures that each domain event is not just a description of state, but the consequence of an intentional business or user operation.
3. Identify Aggregates
Aggregates are central modeling constructs in Domain-Driven Design (DDD). In the context of Event Storming, they serve as consistency boundaries and encapsulate business rules, domain logic, and data integrity for a specific concept within the domain.
An aggregate is not just a collection of objects—it’s a carefully designed unit of consistency and responsibility. It typically consists of:
- One aggregate root (an entity that represents the main access point)
- A set of related entities and value objects
- The invariants (rules) that must always remain true within the boundary
Aggregates ensure that commands and events are processed in a valid, business-consistent way. When a command is issued, it is routed to the appropriate aggregate, which evaluates whether the action can be performed based on its current state. If allowed, the aggregate emits a corresponding domain event.
In Event Storming, once domain events and commands have been captured, teams work together to map them to the aggregates that own the behavior and enforce the rules associated with those interactions.
Typical aggregates in an e-commerce system might include:
Cart— owns the logic of adding/removing items, calculating totals, and applying discountsOrder— governs order creation, confirmation, cancellation, and fulfillmentPayment— controls the initiation, validation, and capture of payment transactions
Each aggregate must be transactionally consistent—any updates inside an aggregate are completed as a single unit. However, aggregates are also decoupled from one another, communicating across boundaries via domain events or application-level coordination.
This approach supports:
- Concurrency control (isolated updates)
- High scalability (independent persistence)
- Service decomposition (microservices alignment)
Aggregates are usually discovered by analyzing which commands trigger which events, and then grouping those pairs based on shared domain behavior and ownership of data integrity. In Event Storming, this often happens once the initial timeline of events and commands is populated.
By clearly defining aggregates, teams gain a better understanding of how to model complexity, ensure data correctness, and support the modularity required for scalable architectures like microservices or modular monoliths.
4. Define Policies
Policies represent the reactive logic within a domain—rules that define how the system should respond when certain domain events occur. While domain events capture what has happened, policies describe what should happen next as a result.
They help answer the critical question: “How does this event lead to another command?”
In Event Storming, policies are typically modeled using the structure:
WHEN [event] THEN [command]
This format makes causal relationships between domain behaviors explicit. For instance:
WHEN payment submitted THEN confirm orderWHEN order confirmed THEN initiate shippingWHEN product added to cart THEN recalculate total
Policies often describe autonomous or asynchronous processes—automated business logic that executes in response to prior events without direct user intervention. They’re especially important in event-driven architectures, where decoupling behavior across services or contexts is a design goal.
In an Event Storming workshop, policies are visualized using a distinct color of sticky notes (often purple) and are placed between the event that triggers them and the command they produce. This ensures a readable cause-effect chain that reinforces how behavior cascades through the domain.
Well-defined policies are crucial because they:
- Encapsulate business rules that span across entities or aggregates
- Enable automation of workflows in response to domain activity
- Support orchestration in distributed systems and microservices
- Help identify integration points between bounded contexts
For example, in a microservices environment, one service might publish an event like Order Shipped. A separate service can subscribe to that event and apply a policy such as WHEN order shipped THEN notify customer, issuing a command to send an email notification.
Policies also help clarify ownership of responsibility—by connecting events to commands, they show who or what is expected to act next. This is especially valuable when modeling cross-domain workflows or designing loosely coupled systems.
In summary, policies are the glue between events (what happened) and commands (what needs to happen next). They model business reaction patterns and ensure that domain workflows are both predictable and extensible, paving the way for responsive, modular systems.
5. Delimit Bounded Contexts
Bounded Contexts (BCs) are one of the most essential strategic patterns in Domain-Driven Design (DDD). They define the semantic boundary within which a particular domain model is valid, consistent, and cohesive. In simple terms, a bounded context provides a clear scope of meaning, behavior, and responsibility—ensuring that the terms, logic, and rules inside are interpreted the same way by everyone working within that boundary.
In the context of Event Storming, once the domain events, commands, and aggregates have been mapped out, the next step is to identify clusters of behavior and concepts that naturally belong together. These clusters are often visualized by drawing boundaries—literally or digitally—around related elements. This exercise reveals the logical seams in the domain where models can diverge without causing confusion or conflict.
For example, in an e-commerce application, you might discover the following bounded contexts:
Ordering: Manages order creation, payment, and trackingCatalog: Handles product listings, prices, and availabilityShipping: Coordinates fulfillment, packaging, and deliveryCustomer Support: Tracks complaints, inquiries, and feedback
Each of these contexts may use similar terminology—such as the word “product” or “order”—but the meaning and behavior of those terms may differ based on their context. That’s exactly what bounded contexts are designed to manage: semantic clarity and modular autonomy.
Bounded contexts serve different purposes depending on architectural style:
- In a modular monolith, each bounded context may become a separate application module, with its own interfaces and internal logic but deployed together.
- In a microservices architecture, each BC becomes the blueprint for a standalone service, with its own persistence, APIs, and development lifecycle.
Key benefits of well-defined bounded contexts include:
- Clear ownership of domain logic and teams
- Decoupled deployment and versioning
- Avoidance of model ambiguity and naming collisions
- Simplified communication and integration between services
Additionally, bounded contexts make it easier to reason about system complexity. By focusing only on the concepts that are relevant within a particular context, developers and domain experts can have sharper, more productive conversations, free from unnecessary dependencies or overloaded abstractions.
When drawing these boundaries during Event Storming, you’re not just separating concerns—you’re laying the foundation for scalable system architecture, effective team collaboration, and long-term software evolution.
Event Storming as a Catalyst for Domain-Driven Design
Event Storming is more than a facilitation technique—it’s a pragmatic enabler of Domain-Driven Design (DDD). DDD offers a powerful set of principles for modeling complex software around business domains, but many of its key concepts—like aggregates, bounded contexts, and ubiquitous language—can remain abstract unless grounded in practical exploration. That’s where Event Storming excels.
By visually mapping out the domain through sticky notes and interactive whiteboarding, Event Storming transforms the theoretical into the tangible. Concepts such as:
- Domain Events – what has happened
- Commands – what initiates change
- Aggregates – who owns consistency and logic
- Bounded Contexts – where meaning is coherent
…are no longer abstract definitions buried in a book or hidden in code—they become visible, interactive artifacts that spark real-world dialogue.
Because the format is accessible to all participants, Event Storming serves as a collaboration bridge between domain experts, developers, architects, product owners, and stakeholders. It facilitates the emergence of a shared mental model, helping technical and non-technical team members align on how the business works—and how the software should reflect that.
Unlike traditional modeling approaches like UML, which require specialized training and often intimidate business users, Event Storming is intentionally informal and inclusive. It avoids rigid syntax in favor of conversational clarity. This lowers the barrier to entry and encourages honest, iterative discovery.
The benefits of this approach include:
- Rapid clarification of ambiguous or misunderstood business logic
- Early identification of service boundaries and integration points
- Consensus on domain language, entities, and behavioral rules
- Increased team ownership over the architecture and design
Event Storming also facilitates emergent modeling. Rather than designing systems in isolation or based on assumptions, it encourages a continuous refinement of the domain model as deeper understanding unfolds. This aligns perfectly with DDD’s emphasis on evolutionary design and frequent collaboration with domain experts.
In short, Event Storming operationalizes DDD. It turns theory into dialogue, dialogue into shared insight, and insight into well-structured, domain-aligned systems.
Applying Hexagonal Architecture to DDD
When applying hexagonal architecture—also known as the Ports and Adapters pattern—to a Domain-Driven Design (DDD) system, the goal is to establish clear separation of concerns and ensure the domain logic remains insulated from external dependencies.
This architectural style provides a robust foundation for building modular, testable, and resilient software systems by defining explicit entry and exit points into the core domain model.
Domain Layer (The Core)
At the heart of the architecture lies the Domain Layer, which contains the pure business logic of the application. This is where:
- Aggregates enforce consistency boundaries and encapsulate domain invariants.
- Value Objects represent immutable descriptive elements (e.g., monetary value, address).
- Domain Services contain business operations that don’t naturally belong to any specific entity.
- Domain Events capture significant occurrences within the business (e.g.,
OrderPlaced,PaymentReceived).
This layer is entirely agnostic to technical frameworks or infrastructure. It defines the interfaces (ports) the application depends on—but not their implementations.
Application Layer (Orchestration)
Sitting just above the domain, the Application Layer acts as a coordinator. It handles use cases and user workflows by:
- Orchestrating commands and delegating execution to aggregates or domain services.
- Managing transactions and interaction sequences.
- Transforming input/output via DTOs (Data Transfer Objects) and handling use case-level validation.
- Using inbound adapters (like controllers or message consumers) to accept external requests.
This layer does not contain business rules, but it is responsible for sequencing and structuring the use of domain logic.
Infrastructure Layer (Adapters and Implementations)
The Infrastructure Layer provides the technical capabilities required to interact with external systems. It includes:
- Outbound adapters, such as repositories (persistence), external service clients, messaging publishers, etc.
- Implementations of interfaces (e.g., saving to a database, calling external APIs) defined in the Domain Layer’s ports.
- Configuration for persistence, messaging, logging, and other I/O concerns.
By inverting dependencies (thanks to the ports and adapters model), the infrastructure layer depends on the domain—not the other way around. This allows teams to swap out technology choices (e.g., switching databases or messaging brokers) without impacting domain logic.
Why It Matters
This architecture brings powerful advantages when paired with DDD:
- Promotes testability by isolating business rules from external systems.
- Supports evolutionary architecture—allowing infrastructure and delivery mechanisms to change over time.
- Enhances modularity and maintainability, especially in systems expected to grow or integrate with multiple platforms.
- Makes domain models resilient to change, preserving business logic even as technologies evolve.
In short, applying hexagonal architecture to a DDD system elevates domain purity, system adaptability, and architectural clarity—all essential traits of enterprise-grade software.
Final Reflections: Why Event Storming Is More Than a Workshop
In today’s enterprise and product environments, complexity isn’t just technical—it’s organizational. Misaligned priorities, fragmented understanding, and siloed communication can erode even the best architecture. When teams struggle to talk about the business clearly, they will inevitably struggle to build the right systems.
That’s why communication—not code—is the first bottleneck in complex domains.
Event Storming directly addresses this root problem. It doesn’t just document requirements or produce diagrams; it creates shared mental models through real-time collaboration. By aligning business stakeholders, architects, and developers around a visual language of events, commands, aggregates, and policies, it becomes a dynamic exercise in collective domain learning.
It shifts the focus from:
- “How should we build?“
to
”What actually happens in the business—and why?”
This makes it not just a design tool, but a cultural intervention—a mindset that puts problem-space exploration before solution-space implementation. It invites everyone to the table and replaces ambiguity with alignment.
If you’re launching a new domain-driven initiative, here’s the advice:
- Don’t start with documentation or system specs—they’ll only reflect what people think they understand.
- Don’t jump to code or frameworks—that’s a recipe for reinforcing bad assumptions.
- Don’t assume the business is already well-understood—it rarely is.
Instead: Start with the business narrative.
- Gather your cross-functional team—developers, designers, analysts, architects, and domain experts.
- Grab a whiteboard (or digital board), sticky notes, and color codes.
- Ask: “What happened?” “Why did it happen?” “What should happen next?”
- Use the structure of events, commands, aggregates, and bounded contexts to discover the shape of the domain.
- Expect surprises. Embrace disagreements. Learn together.
Because the quality of your software depends on the quality of your shared understanding. And Event Storming gives you the most effective structure for building that understanding early—before you’re constrained by code, architecture, or misaligned deliverables.
Concluding
If you’re building software in a complex domain, Event Storming is not optional—it’s essential. It unlocks clarity, fosters trust, and sets the stage for scalable, maintainable, and meaningful systems.
So, don’t wait for consensus in documents or strategy decks. Don’t wait for perfect requirements.
Get your team in a room. Start storming. Solve the right problems—together.